Improving IAM policies
Security is a shared responsibility
As you might have read in my previous posts, public cloud itself should be considered as very secure. For major cloud providers such as AWS security is key. Security incidents would destroy AWS’ business so they are fully committed to prevent this from happening. Their almost unlimited access to security talent, extensive knowledge, years of experience, enormous budget, benefit of building things from scratch etc etc are indicators that security is serious business. And looking at the reported incidents compared to the size and scope of their services is impressive. If you are wondering which incidents have been reported, see here. No doubt about security of the cloud.
This is not preventing security incidents of applications running in the cloud to happen. Despite the number of tools, controls, capabilities and solid security architecture provided by AWS incidents on cloud applications still happen. These type of incidents are caused by human-error or so called security in the cloud. Those security incidents are caused by configuration errors in the space what the customer is responsible for. Compare it to the security of your house. You can have all controls in place, such as proper locks, alarms etc. But if you don’t use them and leave the frontdoor wide open… don’t be surprised if things will go wrong. The same can happen in cloud (or any other IT enviroment) if the implementation is not done correctly. Think of permissive IAM policies, open security groups, etc.
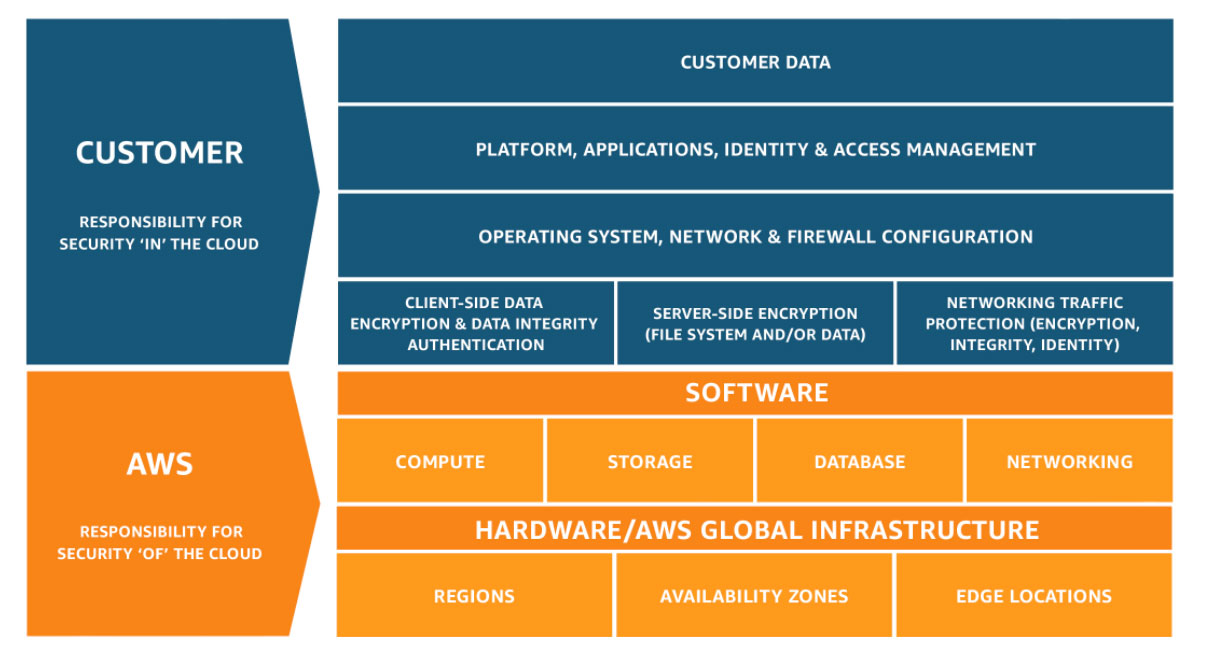 Figure 1: The AWS Shared Responsibility Model
Figure 1: The AWS Shared Responsibility Model
In this blog we will focus on improving IAM policies.
Improve knowledge
Invest in security knowledge Perhaps an open door, but it all starts with knowledge and talent. To level-up your level of knowledge in AWS security, you can explore various resources such as AWS documentation, online courses, certification programs (e.g., AWS Certified Security – Specialty), and industry-specific books and articles. Staying up-to-date with the latest security threats and AWS security features is an ongoing process that can help you adapt to the ever-changing landscape of cloud security.
Run analysis on your IaC
Scan your Infrastructure as Code artifacts. Examples of tools: cdk-nag, AWS CDK plugin – CfnGuardValidator or the scanning capability of Trend Micro Cloud One Conformity.
Those tools typically validate your Infrastructure as Code template against frameworks such as the best practices from the AWS Well-Architected Framework
Use AWS Security Hub, AWS Trusted Advisor and other tools
Insights might change over time and changes can be made unnoticed (e.g. by attackers). Therefore it is important to continously monitory your enviroment on configuration errors. This is called Cloud Security Posture Management and is provided by AWS SecurityHub or 3rd party tools such as Trend Micro Cloud One Conformity. In addition AWS Trusted Advisor can give recommendations on security (available for customers on Business or Enterprise Support plans). Those tools are only powerful when you actually use them.
Be strict on implementing least-privileged policies
Implementing least-privileged policies is a fundamental principle in cybersecurity and access control that helps minimize potential security risks and limit the potential damage that can occur in the event of a security breach. Being strict about implementing least-privileged policies is crucial for maintaining a secure and well-protected environment. When building an application it’s tempting to stop optimizing your IAM policies when your application is working and focus on the next feature of your app. We’ve all been there and got a stack of t-shirts.
- By design don’t accept
Resource: "*"orPrincipal: "*". - Don’t attach policies such as
AdministratorAccess. - Let CDK do heavy lifting by granting access to resources and generating the policies.
- Regularly Test and Assess implemented policies. What you consider as safe today might be unsecure tomorrow. Your knowledge will improve, but also AWS will continuously add new features such as additional fields that can be referenced in policy conditions etc.
- Don’t forget to improve resources policies (encryption keys, data resources etc) and attach/improve IAM Permissions Boundaries.
- Consider Amazon Verified Permissions for fine-grained application-level policies when developing new application.
- Be alert on creating privilege escalation, for example by allowing users to assume other roles or attach wider-policies to their own identities.
Enable AWS account or organization wide security controls
Use AWS Organizations to enable organizational wide controls such as Service Control Policies (SCPs). These controls have priority above IAM controls. SCPs will allow you to define high-level guardrails or disable services/actions that should never be used. SCPs are even applicable to the root user in your AWS account.
AWS Organizations can also be used to deploy and operate AWS Security Hub, CloudTrail and AWS Config etc at scale. These services are essential in monitoring your AWS enviroment. When AWS Organization is used properly all your accounts are managed and monitored centrally. With this you have full visibility and control over what is happening in your accounts.
Monitor your enviroment
Although this is more a detective control it is equally important as preventive controls. Defining IAM policies is still a user responsibility and, in contrast with computers, we humans tend to be error-prone. And our attackers are creative.
Monitoring is essential for:
- Improving hygiene by removing unused IAM entities
- Detecting unexpected behaviour
- Detecting (attempts) of attacks
- Staying in control your cloud security
Examples of AWS services that are essential for monitoring are: AWS Config, AWS Security Hub, AWS CloudTrail, Amazon GuardDuty.
Verdict
In conclusion, the responsibility for security in cloud computing is a shared responsibility, with cloud providers like AWS offering highly secure infrastructure, but organizations also playing a crucial role in safeguarding their assets. AWS demonstrates its commitment to security through extensive resources, talent, and experience.
Despite the robust security measures provided by AWS, incidents can still occur due to human errors and misconfigurations, often referred to as “security in the cloud.” Organizations can enhance their cloud security by adopting several key practices:
Invest in knowledge: Continuous learning and staying informed about AWS security features and evolving threats are fundamental to maintaining a secure cloud environment.
Analyze Infrastructure as Code: Scan Infrastructure as Code artifacts for compliance with best practices, using tools like cdk-nag and AWS CDK plugins.
Leverage security tools: Utilize AWS Security Hub, AWS Trusted Advisor, and other monitoring tools to detect and prevent configuration errors and security threats.
Implement least-privileged policies: Strictly adhere to the principle of least privilege in access control to minimize security risks and continually test and assess policies for improvements.
Enable AWS Account-wide Controls: Use AWS Organizations to establish Service Control Policies (SCPs) that define high-level security guardrails across all AWS accounts, ensuring consistent security measures.
Monitor Continuously: Employ monitoring and detective controls to detect unusual behavior, potential attacks, and improve overall cloud security hygiene
By following these practices, organizations can contribute to a secure cloud environment and effectively mitigate security risks, while benefiting from AWS’s robust security infrastructure and expertise. Remember that security is an ongoing process that requires vigilance and adaptation to evolving threats and technologies.
